To continue reading this article you must be a paid subscriber.
Subscribe to MDMAlready Subscribed? Click here to log-in | Forgot your password?
Related Posts
-
Flow-Zone is the premier distributor of pipe, valves, fittings, instrumentation, controls and measurement equipment for…
-
The business will be integrated into Jasons Industrial segment within Osborn.
-
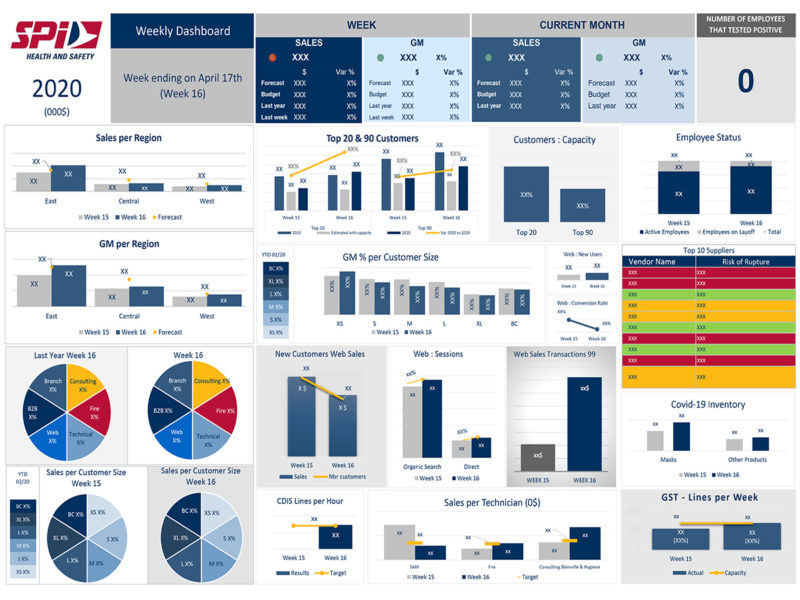
Executives at the health and safety distributor review key performance indicators each week in order…